Lab 2 - Reconnaissance
In this lab, you are going to do reconnaissance on the University of the Pacific using a variety of publicly available websites or open source software tools.
Activities
Part 1 - Autonomous Systems (AS)
Many organizations, including University of the Pacific, have configured their networks as Autonomous Systems (AS), providing them the ability to use multiple internet service providers and route traffic between them as desired.
References:
There are many online tools that allow you to look up Autonomous System information for a given organization name or domain name, such as:
- MXToolbox - https://mxtoolbox.com/asn.aspx (Tip: Search for an IP address)
- HackerTarget - https://hackertarget.com/as-ip-lookup/ (Tip: Search for an IP address)
- ANSLookup - https://asnlookup.com/ (Tip: Search for "UOP")
Deliverables:
- What is the Autonomous System number for University of the Pacific?
Tip 1: It's easy to make a mistake here. For MXToolbox and HackerTarget, you have to search for an IP address that is within the ASN. What's a good IP address? Find the IP address for some system that you know is hosted locally and not in a cloud provider like Amazon Web Services. For Pacific, for example,
locksmith.pacific.eduis hosted locally.
Tip 2: If you are on-campus while doing this lab, be careful! Your local system will see a private IP address for the locksmith system of the form 10.x.x.x.x. For your ASN lookup, you want the public IP address of the locksmith system. Use an off-campus tool like MXToolbox to obtain that IP address.
CHECKPOINT: Did you find the correct Pacific ASN of the form 18xxx? If not, double-check your work above before continuing with the rest of the lab. You can verify the ASN you found at https://iplocation.io/asn-whois-lookup
Classless Inter-Domain Routing (CIDR) is a method for allocating IP addresses and IP routing. CIDR notation is a compact representation of an IP address and its associated routing prefix. The notation is constructed from an IP address, a slash (/) character, and an integer.
For example, the CIDR entry 18.5.27.0/24 means that the upper 24 bits of the address (18.5.27) stay constant and the lower 8 bits are variable and represent computers within the subnet. 18.5.27.0 is the first address and 18.5.27.255 is the last address, for a total of 256 possible addresses in that range.
Deliverables:
- What is the CIDR-format subnet that is associated with Pacific's Autonomous System number? Provide your answer in the format
a.b.c.d/n
Tip: MXToolbox and HackerTarget can search by AS number and show the associated CIDR ranges.
Part 2 - Shodan
Shodan is a search engine for finding specific devices, and device types, that exist online. The most popular searches are for things like webcam, linksys, cisco, netgear, SCADA, etc. It works by scanning the entire Internet and parsing the banners that are returned by various devices. Using that information, Shodan can tell you things like what web server (and version) is the most popular, or how many anonymous FTP servers exist in a particular location, and what make and model the device may be.
Fun links:
- Awesome Shodan Search Queries: https://github.com/jakejarvis/awesome-shodan-queries
- Getting the Most Out of Shodan Searches (SANS Penetration Testing blog): https://www.sans.org/blog/getting-the-most-out-of-shodan-searches/
Create a Shodan Login (required to use most of the site features), and then answer the following questions.
Deliverables:
Start a new Shodan search:
- Search for hosts with the domain name
pacific.edu. How many did Shodan find?
Tip: Use thehostname:filter for your query.
Start a new Shodan search and do these questions as a sequence (as they get increasing specific):
- Search for hosts within Pacific's CIDR subnet. How many did Shodan find?
Tip: Use thenetfilter for your query. Also, If you find less that 10 here, give-or-take, double-check your CIDR subnet above. - Of the hosts found in the previous question, how many of those are running
Microsoft IIS httpdas their web server?
Tip: You can drill down in the left panel, or append theproduct:"xxx"filter to your query. - Of the hosts found in the previous question, how many of those results are servers running
version 10.0ofMicrosoft IIS htttpd?
Tip: You can drill down in the left panel, or add theversion:"nn.n"filter to your query. - Of the hosts found in the previous question, several of them have SSL certificates (for HTTPS). What are the common names (i.e. domain names) that those certificates are issued for?
- For the previous SSL certificate question, what was the Shodan search query you entered? (Even if you were drilling down via the GUI, the query in the search box at the top is updated with each additional filter that was added)
Start a new Shodan search:
- What is the IP address of one of Pacific's Network Time Protocol (NTP) servers? There are several, any valid IP will be accepted.
Tip: You can either specifyntpin your query, or addport:123to specify the port that NTP servers commonly use
Tip: These NTP servers do not have hostnames, so you will need to search within Pacific's CIDR subnet to find them. - For the previous NTP question, what was the Shodan search query you entered?
Part 3 - Whois
The WHOIS system allows access to directory information stored by domain name registrars.
Using whois (in your Kali VM), find information on the domain name "pacific.edu".
$ whois pacific.eduDeliverables:
- What is the email address associated with the technical contact for the domain name
pacific.edu? - What are the authoritative name servers for the domain
pacific.edu? (These are the name servers that provide the final official translation between the domain name pacific.edu and its IP address)
Part 4 - DNS
Sublist3r is a DNS enumeration tool. It uses a combination of internet search engines and (optionally) brute force guessing to provide a list of subdomains given a starting domain.
References:
First, signup for a free account at VirusTotal. After registering and logging in, copy your API key from your profile.
Second, install Sublist3r (in your Kali VM) and a code patch to fix integration with VirusTotal.
# Install Sublist3r
$ sudo apt install sublist3r
# Patch Sublist3r following instructions on this PR
# https://github.com/aboul3la/Sublist3r/issues/194
$ wget https://raw.githubusercontent.com/aboul3la/Sublist3r/3cb826c2f36f4972dfd286c704efc07de3a7f94c/sublist3r.py
$ sudo mv sublist3r.py /usr/lib/python3/dist-packages/sublist3r.py
# Configure your VirusTotal API key, which will be used to Sublist3r
$ export VT_APIKEY="<your-api-key-copied-from-virustotal>"With sublist3r, obtain an incomplete but still lengthy list of subdomains for the domain name "pacific.edu".
# Run the enumeration
$ sublist3r --domain pacific.eduDeliverables:
- Provide a list of 5 subdomains to pacific.edu that are particularly "interesting" and that you didn't know existed prior to running the scan. (No wrong answers here)
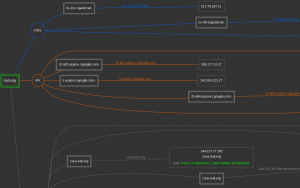
The DNS Dumpster is a similar tool with a web interface. Use the DNS Dumpster to obtain a list of subdomains for the domain name "kali.org".
Deliverables:
- Upload the "Domain Map" image from DNS Dumpster that summarizes the search results for "kali.org"
Fierce is a domain name scanner to help locate non-contiguous IP space and hostnames against specified domains. In other words, given a domain name, it will find subdomains and locate nearby servers ("nearby" based on IP address) that may or may not actually share the same domain name. This tool does not perform exploitation and does not scan the whole internet indiscriminately. It is meant specifically to locate likely targets both inside and outside a corporate network. Because it uses DNS primarily you will often find mis-configured networks that leak internal address space.
References:
Use Fierce (in your Kali VM) to do a DNS scan:
# BUGFILE SPRING 2025 ONLY
# The latest Fierce version fixes an error in recent Python.
# However, Kali 2024.4 doesn't have the latest Fierce in its package library.
# Install via pip:
sudo apt install pipx
pipx install fierce
~/.local/bin/fierce --domain pacific.edu --dns-server 8.8.8.8
# TYPICAL COMMAND (once Kali updates to the latest Fierce release)
$ fierce --domain pacific.edu --dns-server 8.8.8.8The command above explicitly uses Google's Public DNS server (8.8.8.8) instead of whatever your local DNS server is. This is because Pacific uses split-horizon DNS, and thus on-campus users see different IP addresses than off-campus users. By specifying a clearly off-campus DNS server, you should see the same IP addresses regardless of whether you are on or off campus.
Deliverables:
- What is the IP address for the host
locksmith.pacific.edu? (As seen from off-campus) - What is the IP address for the host
tiger.serv.pacific.edu? (As seen from off-campus)
Part 5 - SSL Certificates
SSL certificates can be a useful source of hostnames that may be of interest in a penetration test. You can inspect SSL certificates manually in your web browser, or by using various online resources, such as:
Deliverables:
- For the hostname
www.pacific.edu, what are the "alternative names" or "DNS Names" listed in the SSL certificate? This would be a list of other host names that are also signed/secured by the same certificate. You can check this either in your web browser or for one of the online query tools listed.