Quarantine Network Usage
Q: How can I safely run malicious software in the lab?
A: Very carefully...
Rules
The are a few key rules when running malicious software / malware in the lab:
Rule 1: Malware should only be run inside of a virtual machine, never on the host OS. This makes it easy to start, stop, reset to an earlier snapshot, or nuke from orbit. And, it allows the same PC to be used by subsequent students for non-malware related activities.
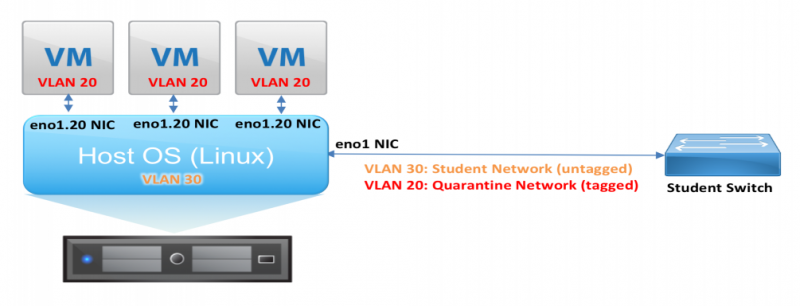
Rule 2: The malware-infected virtual machine should only have access to the quarantine network (VLAN 20). The malware VM should never be connected to the student network, not via bridging, and not via NAT.
Rule 3: Computers that are not malware infected should not be connected to the quarantine network. For example, the host OS should only be connected to the student network.
Instructions
In the context of the student desktop PCs in the lab, these rules should be implemented as follows.
Normal operation (non-malware):
- The wired Ethernet adapter on the PCs is named
eno1. (This is short for 'en' Ethernet, 'o' Onboard NIC, '1' Interface 1). This NIC sees both student VLAN traffic (untagged here, but VLAN 30 at the router) and quarantine VLAN traffic (tagged, VLAN 20). By default, only the untagged VLAN (for the student network) is visible to the host OS. - DHCP is configured in the Linux host OS on the
eno1interface. The DHCP request in untagged and goes to the student VLAN, and the host OS is assigned an IP on the student subnet.
Quarantine operation (malware):
Malware should only be run inside a virtual machine, never on the host / bare metal OS. During this period, the host OS should be configured to see the existence of the quarantine VLAN but not assign an IP address in order to actively pass traffic. Use the Network Manager GUI to create a new virtual interface called eno1.20, and connect it to VLAN 20 on physical interface eno1. This new virtual interface is only for the quarantine VLAN, not student VLAN. All traffic sent using this new interface will be automatically tagged for the quarantine VLAN, and all traffic received from the quarantine VLAN will be automatically untagged.
To create the virtual interface with the Network Manager utility, follow this process:
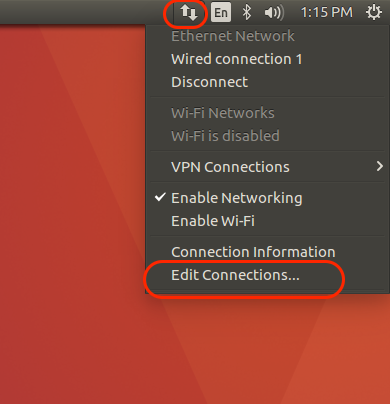 |
Choose "Edit Connections" from the Network Manager tool in the upper right-hand corner |
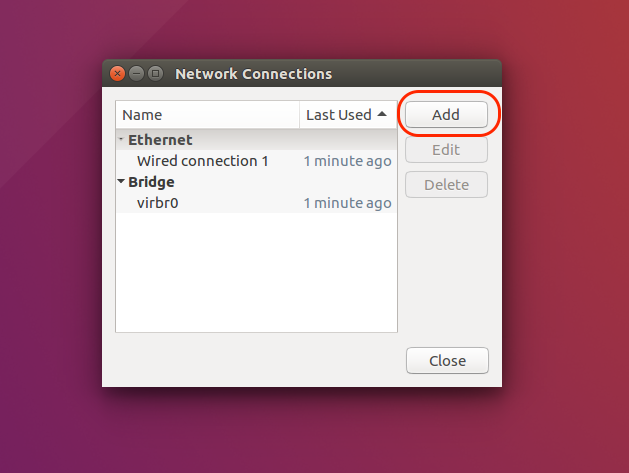 |
Choose "Add" to create a new connection |
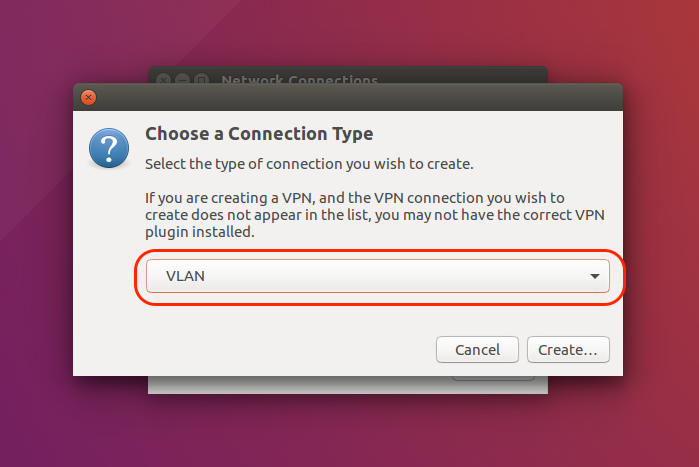 |
Choose "VLAN" to create a new VLAN connection |
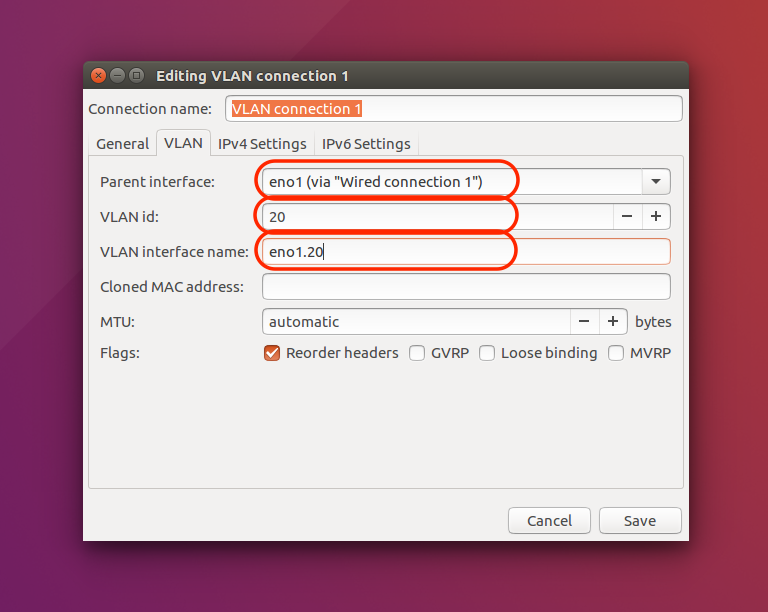 |
For Parent Interface, choose eno1.For VLAN ID, enter 20 (for Quarantine VLAN)For VLAN Interface Name, enter eno1.20 |
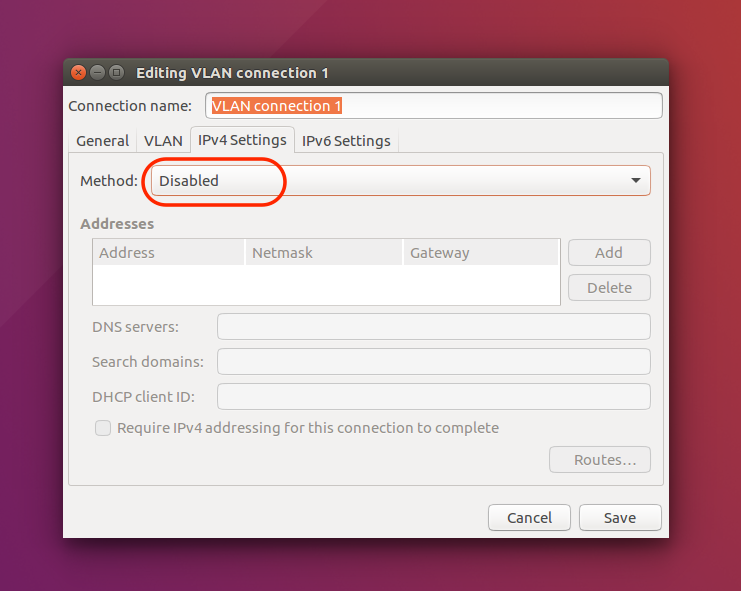 |
Under the IPv4 Settings tab, choose method Disabled.We do NOT want the host OS obtaining an IPv4 address on the quarantine network! |
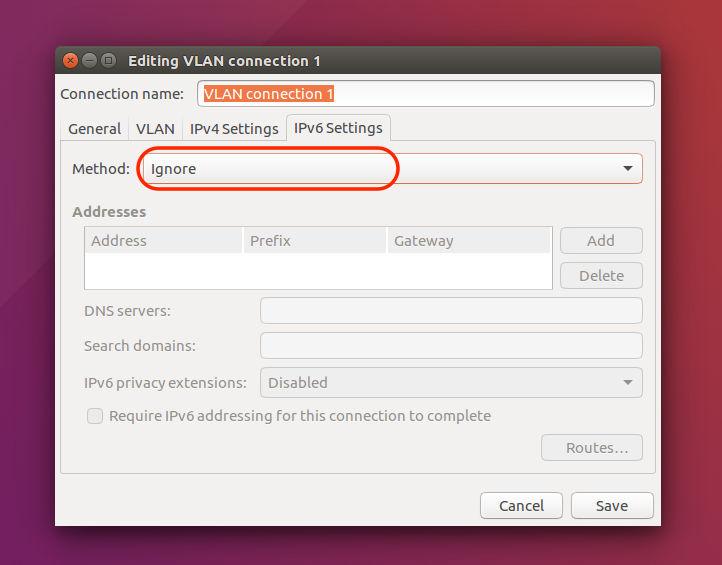 |
Under the IPv6 Settings tab, choose method Ignore.We do NOT want the host OS obtaining an IPv6 address on the quarantine network! |
To attach a KVM-based VM to the Quarantine network using the Virtual Machine Manager GUI, click on the Info (I) button, find the NIC on the left-hand side, and choose the eno1.20 virtual interface you just created. Make sure that it is in bridge mode.
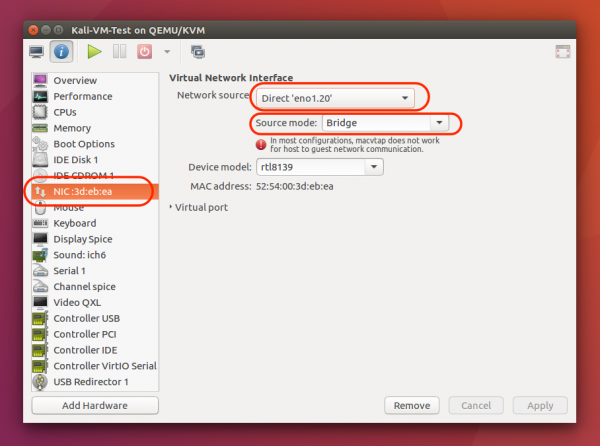
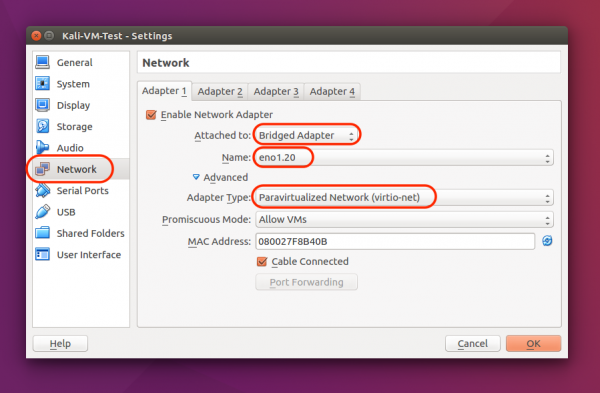
To attach a Virtual Box-based VM to the Quarantine network, go to the VM settings, find the Network tab on the left-hand side, and select Bridged Adapter with name eno1.20 You may also need to change the adapter type to Paravirtualized Network (virtio-based) and enable Promiscuous Mode for the guest.
Alternate method:
The virtual interface can also be created at the command line, but doing so will result in the Network Manager utility ceasing to manage this interface, which is not desirable and/or will be confusing for future students.
sudo ip link add link eno1 name eno1.20 type vlan id 20
# This command is temporary and will not persist after a reboot/shutdown
#
ip -d link show eno1.20 # View virtual interface
sudo ip link delete eno1.20 # Delete virtual interfaceAfter creating the virtual interface, ensure that you do not assign it an IP address (manually, or via DHCP) in the host OS. This quarantine interface is only present in the host OS so that it can be mapped to a virtual machine.
Verification
Before running any malware, verify your configuration:
From the Host OS:
You should only be able to see the STUDENT network (.30.x), not the Quarantine (.20.x) or INSTRUCTOR (.40.x) network.
nmap -sP 10.1.20.0/24 # Should see NOTHING (beyond router)
nmap -sP 10.1.30.0/24
nmap -sP 10.1.40.0/24 # Should see NOTHING (beyond router)
ping -c 4 google.com # Should have public Internet accessFrom the Guest OS (malware host):
You should only be able to see the QUARANTINE network (.20.x), not the STUDENT (.30.x) or INSTRUCTOR (.40.x) networks.
nmap -sP 10.1.20.0/24
nmap -sP 10.1.30.0/24 # Should see NOTHING (beyond router)
nmap -sP 10.1.40.0/24 # Should see NOTHING (beyond router)
ping -c 4 google.com # Should have public Internet access